Introduction to Zero Trust Architecture
In today’s digital landscape, where cyber threats are evolving rapidly, traditional security models are no longer sufficient. Enter Zero Trust Architecture, a revolutionary approach that assumes no user or device can be trusted by default, regardless of their location or network connection. This model emphasizes continuous verification, least-privilege access, and robust monitoring to safeguard sensitive data and resources.
Zero Trust Architecture shifts the focus from perimeter-based defenses to a more granular, identity-centric strategy. By implementing this framework, organizations can significantly reduce the risk of data breaches and lateral movement by attackers. Whether you’re in cloud environments, hybrid setups, or remote work scenarios, understanding Zero Trust Architecture is essential for modern cybersecurity.
As cyber attacks become more sophisticated, adopting Zero Trust Architecture isn’t just a trend—it’s a necessity. This guide explores its principles, pillars, implementation steps, and more, helping you build a resilient security posture.
What is Zero Trust Architecture?
Zero Trust Architecture (ZTA) is a cybersecurity framework that operates on the principle of “never trust, always verify.” It eliminates the concept of implicit trust within networks, treating every access request as potentially hostile, whether from inside or outside the organization.
Unlike traditional models that rely on firewalls and VPNs to create a secure perimeter, Zero Trust assumes that threats can exist anywhere. It enforces strict access controls, continuous authentication, and authorization for every user, device, and application attempting to connect to resources.
At its core, Zero Trust Architecture is designed to prevent data breaches by limiting internal lateral movement of threats. It encompasses identity management, endpoint security, and real-time monitoring, making it ideal for dynamic environments like cloud computing and remote workforces.
The term “Zero Trust” was popularized by Forrester Research in 2010, but its principles have roots in earlier security concepts. Today, it’s endorsed by organizations like NIST, which defines it as an end-to-end approach to resource and data security.
In practice, Zero Trust Architecture uses tools like multi-factor authentication (MFA), micro-segmentation, and AI-driven risk assessment to evaluate each request contextually. This ensures that access is granted only when necessary, reducing the attack surface.

Core Principles of Zero Trust Architecture
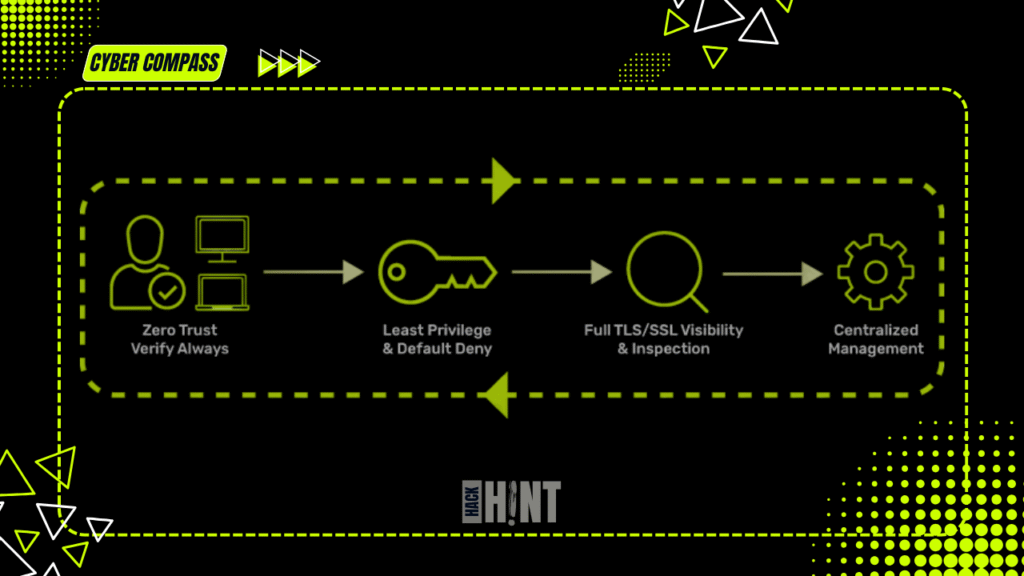
Zero Trust Architecture is built on three foundational principles outlined by NIST and other experts, ensuring a proactive and adaptive security stance.
Verify Explicitly
- This principle mandates continuous verification of all access requests based on multiple factors, including user identity, device posture, location, and behavior. Authentication and authorization occur before any session is established, using real-time data to assess risks.
- For instance, even if a user is on a corporate network, their request is scrutinized as if they were external. This dynamic evaluation prevents unauthorized access by adapting to changing conditions.
Use Least Privilege Access
- Access is granted on a need-to-know basis, minimizing what users can reach. Just-In-Time (JIT) and Just-Enough-Access (JEA) mechanisms ensure privileges are temporary and context-specific, enforced through granular policies.
- This reduces the blast radius of potential breaches, as compromised accounts have limited impact. Identity-based segmentation further refines this by tying access directly to verified identities.
Assume Breach
- Zero Trust operates under the assumption that breaches are inevitable. It focuses on containing threats through micro-segmentation, end-to-end encryption, and continuous monitoring to detect anomalies early.
- By treating the network as hostile, organizations can implement robust incident response and minimize damage from internal threats.
- These principles collectively transform security from a static perimeter to a fluid, risk-aware system.
Key Pillars of Zero Trust Architecture
Zero Trust Architecture rests on five key pillars that secure various aspects of an organization’s IT ecosystem.
Identity
- Identity management is central, involving SSO, MFA, and IAM systems to verify human and non-human entities. Attributes like user behavior and privileges are continuously evaluated.
Devices
- All devices, from laptops to IoT gadgets, are assessed for compliance and posture before granting access. This includes BYOD policies to handle unmanaged assets.
Networks
- Networks are secured through encryption, micro-segmentation, and traffic monitoring, eliminating implicit trust zones.
Applications and Workloads
- Applications are monitored at runtime for behavioral anomalies, ensuring secure deployment across on-premises and cloud environments.
Data
- Data protection involves classification, encryption, and access controls to prevent unauthorized exfiltration, whether at rest or in motion.
- These pillars provide a comprehensive framework for implementing Zero Trust.

How Zero Trust Architecture Differs from Traditional Security Models
Traditional security relies on a “castle-and-moat” approach, where trust is granted once inside the perimeter via firewalls and VPNs. However, this fails in modern, distributed environments.
In contrast, Zero Trust Architecture has no perimeter every request is verified dynamically, preventing lateral movement. Traditional models assume internal safety, while Zero Trust assumes breaches and enforces continuous authentication.
Scalability is another difference: Traditional setups struggle with cloud and mobile, but Zero Trust adapts seamlessly.
A comparison table highlights these distinctions:
| Aspect | Traditional Architecture | Zero Trust Architecture |
|---|---|---|
| Trust Model | Implicit trust inside perimeter | No implicit trust; always verify |
| Access Control | Broad after login | Per-session, least privilege |
| Visibility | Limited, especially encrypted traffic | Full, continuous monitoring |
| Scalability | Centralized, hard to scale | Flexible for cloud and hybrid |
| Threat Assumption | External threats only | Breaches assumed everywhere |
This shift makes Zero Trust more resilient against sophisticated attacks.
Benefits of Implementing Zero Trust Architecture
Adopting Zero Trust Architecture offers numerous advantages for organizations.
- First, it enhances security by reducing the attack surface through strict verification, limiting breach impacts.
- It improves compliance with regulations like GDPR and HIPAA by enforcing granular access controls and audit trails.
- Cost savings arise from preventing costly data breaches and streamlining access management.
- Zero Trust also boosts user experience with seamless, context-aware access, supporting remote work without VPN hassles.
- Finally, it future-proofs security against emerging threats like AI-driven attacks and IoT vulnerabilities.
Challenges in Adopting Zero Trust Architecture
While beneficial, implementing Zero Trust isn’t without hurdles.
- Legacy systems may not integrate easily, requiring phased migrations.
- Cultural resistance from teams accustomed to traditional models can slow adoption.
- High initial costs for tools and training are common, though long-term savings offset this.
- Ensuring comprehensive visibility across hybrid environments demands advanced monitoring.
- Overcoming these involves starting small, with pilot programs focused on high-risk areas.
Steps to Implement Zero Trust Architecture
Implementing Zero Trust is a journey, not a one-time event.
Step 1: Visualize
- Map all assets, users, and access points to identify risks. Categorize data, devices, and applications.
Step 2: Mitigate
Step 3: Optimize
- Extend protections to all environments, refine policies based on monitoring, and ensure minimal disruption.
- Use tools like policy engines and threat intelligence for dynamic decisions.
- Regular audits and employee training are crucial for success.
Real-World Examples of Zero Trust Architecture
- Google’s BeyondCorp initiative pioneered Zero Trust by treating all networks as untrusted and verifying device health.
- The U.S. Department of Defense adopted Zero Trust to secure classified networks, reducing breach risks.
- Companies like Zscaler provide cloud-based Zero Trust platforms, enabling secure access without VPNs.
- These examples show how Zero Trust scales across industries, from tech giants to government agencies.
Future Trends in Zero Trust Architecture
- As of 2025, Zero Trust is evolving with AI and machine learning for automated risk assessments.
- Integration with quantum-resistant encryption will counter emerging threats.
- Zero Trust for IoT and edge computing will become standard, addressing decentralized environments.
- Sustainability-focused implementations will optimize resource use in security operations.
- Organizations should stay agile, updating strategies with regulatory changes and tech advancements.
To make Zero Trust actionable, start by assessing your current security gaps. Conduct a risk audit to prioritize assets. Integrate tools like identity providers (e.g., Okta) and security platforms (e.g., Microsoft Azure AD) for seamless verification.
External Links:
- NIST Special Publication 800-207 on Zero Trust Architecture (DoFollow): https://nvlpubs.nist.gov/nistpubs/specialpublications/NIST.SP.800-207.pdf
- Zscaler Guide to Zero Trust (DoFollow): https://www.zscaler.com/resources/security-terms-glossary/what-is-zero-trust-architecture
- Microsoft Zero Trust Overview (DoFollow): https://learn.microsoft.com/en-us/security/zero-trust/zero-trust-overview
FAQ
What is the main goal of Zero Trust Architecture?
The primary goal is to prevent data breaches by verifying every access request and assuming no inherent trust, reducing lateral movement of threats.
How does Zero Trust Architecture handle remote work?
It secures remote access through continuous verification of identity, device health, and context, eliminating the need for traditional VPNs.
Is Zero Trust Architecture suitable for small businesses?
Yes, scalable solutions like cloud-based platforms make it accessible, starting with high-risk areas like email and data access.
What tools are essential for Zero Trust implementation?
Key tools include IAM systems, MFA, micro-segmentation software, and AI-driven monitoring platforms.
How does Zero Trust differ from VPN-based security?
Unlike VPNs that grant broad access once connected, Zero Trust enforces per-request verification for least-privilege access.