Introduction
Windows 11 users have reported SSDs disappearing mid-transfer, data corruption, and even bricked drives after installing KB5063878 (24H2), but the emerging consensus points to unstable engineering firmware on certain SSDs—not Windows—as the most likely trigger. This explains the irregularity of failures, the difficulty reproducing them in labs, and why users with evaluation or gray-channel drives were hit hardest. The focus should be on verifying and updating to stable, retail-grade firmware while maintaining robust backups and conservative storage practices.
The Symptoms: Vanishing Drives and Corrupted Data
Vanishing drives
- SSDs vanished from Windows during large transfers and reappeared after reboot or power-cycle, signaling controller resets under heavy I/O.
- Some systems showed the drive as a boot option but not as a detected device, indicating low-level instability rather than a simple OS enumeration glitch.
Corrupted or unreadable data
- Users reported unreadable or corrupted files after long writes, consistent with firmware mishandling of queue depths, timeouts, or FTL metadata updates.
- A subset saw permanent loss where Windows marked the drive unreadable and it could not be recovered through standard tools.
Patterns and affected models
- Failures were more common when drives exceeded roughly 60% capacity, where garbage collection and wear-leveling pressure rise during sustained writes.
- Incidents spanned DRAM-less and DRAM-equipped SSDs, frequently tied to evaluation or reviewer units that may carry pre-release firmware.
Microsoft’s Investigation: “Not Our Bug”
Microsoft telemetry and stress testing did not find a causal link between KB5063878 and widespread SSD corruption, which fits the pattern observed on production hardware and firmware. The inability to reproduce issues under lab conditions suggests the problem resides in certain firmware builds rather than the Windows update mechanisms. This also explains the gap between community anecdotes and vendor test outcomes.
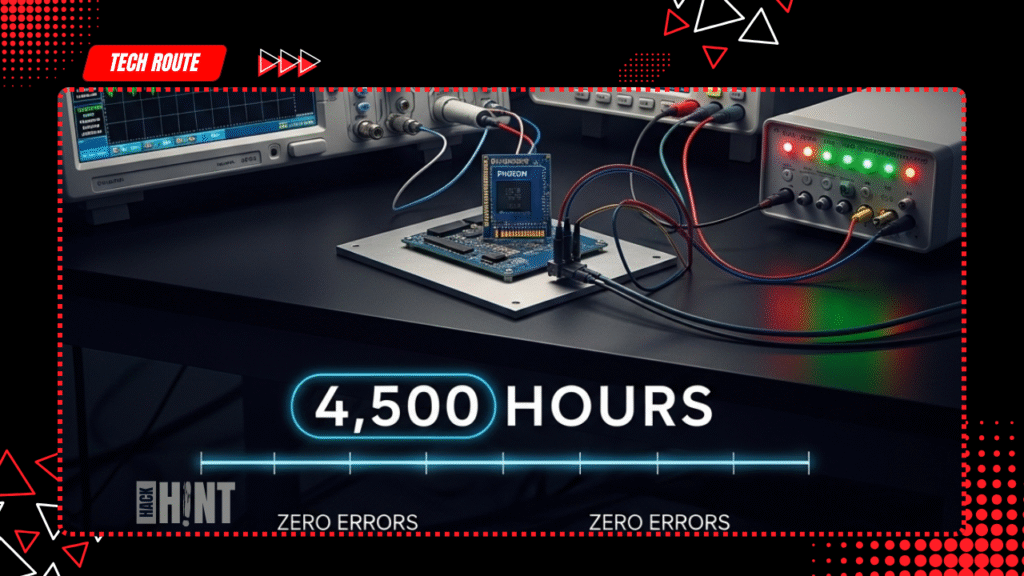
Phison’s 4,500-Hour Stress Test
Phison ran more than 4,500 hours of testing across thousands of cycles and multiple controllers, reporting no failures on drives with retail firmware. The company stressed that consumer SSDs shipping through official channels were stable under heavy read/write loads. This strongly differentiates retail firmware behavior from early or engineering builds used in development or media sampling.
Engineering Firmware: The Missing Piece
What is engineering firmware?
Engineering (pre-release) firmware is development code used for internal testing and validation. It can include debug hooks, incomplete optimizations, and features not hardened for production. Unlike retail firmware, it does not receive the same breadth of edge-case validation and is not intended for public distribution or production deployment.

Why is it surfacing now?
A PC DIY community traced failures to SSDs running pre-release engineering firmware; vendors reportedly reproduced crashes only on these builds and not on retail images. Windows 11 24H2 introduced file operation patterns that placed sustained pressure on storage subsystems, exposing latent fragility in non-final firmware, especially on drives more than ~60% full. This reconciles conflicting observations: Microsoft could not reproduce the problem on production firmware, and Phison’s retail tests remained stable.
How to Check and Protect Your SSD
- Verify firmware version:
- Use the SSD vendor’s toolbox or system utilities to read the current firmware build.
- Compare against the latest retail version on the manufacturer’s support site.
- If the label references preview/beta/ENG or does not match the channel build, update immediately.
- Back up critical data:
- Keep current backups to cloud, NAS, or external HDDs before doing firmware updates or large transfers.
- Automate recurring backups to reduce the blast radius of sudden failures.
- Update to retail firmware:
- Download only from official vendor portals and apply the latest production firmware.
- Avoid beta/test images unless the manufacturer explicitly instructs to use them for a targeted fix.
- Reduce stress until patched:
- Avoid very large transfers on drives above 60% capacity.
- Maintain 15–20% free space to give the controller headroom for garbage collection and wear-leveling.
- Ensure adequate cooling and airflow for NVMe drives to prevent thermal compounding.
- Check platform firmware:
- Update motherboard UEFI/BIOS to the latest stable version to eliminate platform-level contributors.
- Re-test under load after updates to confirm stability.
Solutions and Best Practices (NIST-aligned)
Asset and configuration management
- Maintain an inventory of SSD models, controller families, and firmware baselines across endpoints.
- Standardize on vendor-approved retail firmware and document update lineage, aligning with NIST SP 800-53 CM controls.
Change control and ring testing
- Pilot Windows updates and firmware changes in rings (dev, pilot, production) and validate storage I/O behaviors before broad deployment.
- Gate releases on SMART health metrics, error logs, and stability under representative workloads.
Data protection and recovery
- Enforce routine, automated backups with periodic restore drills to validate integrity and RTO/RPO assumptions.
- Use 3-2-1 principles where practical for critical data and endpoints.
Monitoring and telemetry
- Enable SMART monitoring and error logging; track firmware versions centrally to correlate anomalies with specific builds.
- Alert on spikes in media errors, command timeouts, resets, and thermal events.
Supply chain hygiene
- Procure SSDs through authorized channels; avoid gray-market or evaluation units that may ship with engineering firmware.
- Require vendor attestations that devices ship with the latest retail firmware.
Thermal and capacity headroom
- Use appropriate heatsinks and ensure airflow for high-performance NVMe drives.
- Keep 15–20% free space to reduce write amplification and controller wear under heavy workloads.
Incident response
- At the first sign of corruption or disappearing drives, stop heavy transfers, capture logs, and make a fresh backup.
- Flash the latest retail firmware and update motherboard UEFI/BIOS, then re-validate under load before resuming normal operations
Additional Insights and Trends
- Community-led investigations were key to isolating the variable: engineering firmware versus retail firmware on otherwise similar drives.
- Media and influencer units disproportionately carried early firmware, explaining why the most dramatic failures appeared in reviews rather than among mainstream retail users.
- As users verify and migrate to retail firmware, reports of catastrophic corruption appear to narrow to niche configurations.
Final Thoughts and Key Takeaway
The preponderance of current evidence indicates engineering firmware instability—not Windows 11 KB5063878—is behind most SSD corruption incidents, aligning Microsoft’s findings with community tracing and Phison’s retail-firmware stress results. Actionably, ensuring production firmware, maintaining backups, and avoiding gray‑market hardware eliminate the highest-risk vectors seen in these reports.
Key takeaway: If an SSD fails after KB5063878, verify and update to stable retail firmware before blaming Windows—engineering builds were never intended for consumer workloads.
FAQ
Does Windows 11 KB5063878 corrupt all SSDs?
No, current evidence points to engineering or pre-release SSD firmware as the common factor, while Microsoft reports no causal link to the update.
How can engineering firmware reach users?
Through evaluation units, gray-market channels, or units shipped without a final firmware flash—situations noted by community investigations and coverage.
Can data be recovered after corruption?
Sometimes; drives that still enumerate may be recoverable, but in some cases recovery fails—underscoring the need for backups before any firmware work.
Should systems be rolled back from Windows 11 to Windows 10?
Not necessary if the SSD runs stable retail firmware; the issue centers on pre-release firmware stability, not a general Windows bug.
Does this affect all SSD brands?
No; incidents cluster around drives with pre-release firmware, while production firmware across major vendors has tested stable in repeated stress tests.
- This Week in Cybersecurity: Chrome Zero-Days, Record DDoS & Major Arrests (Sep 22-28, 2025)
- This Week in Cybersecurity: Major Attacks, Zero-Days & Critical Threats (Sep 15-21, 2025)
- 100+ Cybersecurity Project Ideas (2025) : Beginner to Expert Projects
- This Week in Cybersecurity: Top Threats, Deepfakes & Regulatory Updates (Sep 8–14, 2025)
- The Truth Behind Windows 11 SSD Corruption: KB5063878